Tech
New Blast-RADIUS attack bypasses widely-used RADIUS authentication

Blast-RADIUS, an authentication bypass in the widely used RADIUS/UDP protocol, enables threat actors to breach networks and devices in man-in-the-middle MD5 collision attacks.
Many networked devices (including switches, routers, and other routing infrastructure) on enterprise and telecommunication networks use the authentication and authorization RADIUS (Remote Authentication Dial-In User Service) protocol, sometimes tens of thousands of devices on a single network.
Among its wide range of applications, the protocol is used for authentication in DSL and FTTH (Fiber to the Home), 802.1X and Wi-Fi, 2G and 3G cellular roaming, 5G DNN (Data Network Name), private APN and VPN, and critical infrastructure networks.
Blast-RADIUS exploits a new protocol vulnerability (CVE-2024-3596) and an MD5 collision attack, allowing attackers with access to RADIUS traffic to manipulate server responses and add arbitrary protocol attributes, which lets them gain admin privileges on RADIUS devices without requiring brute force or stealing credentials.
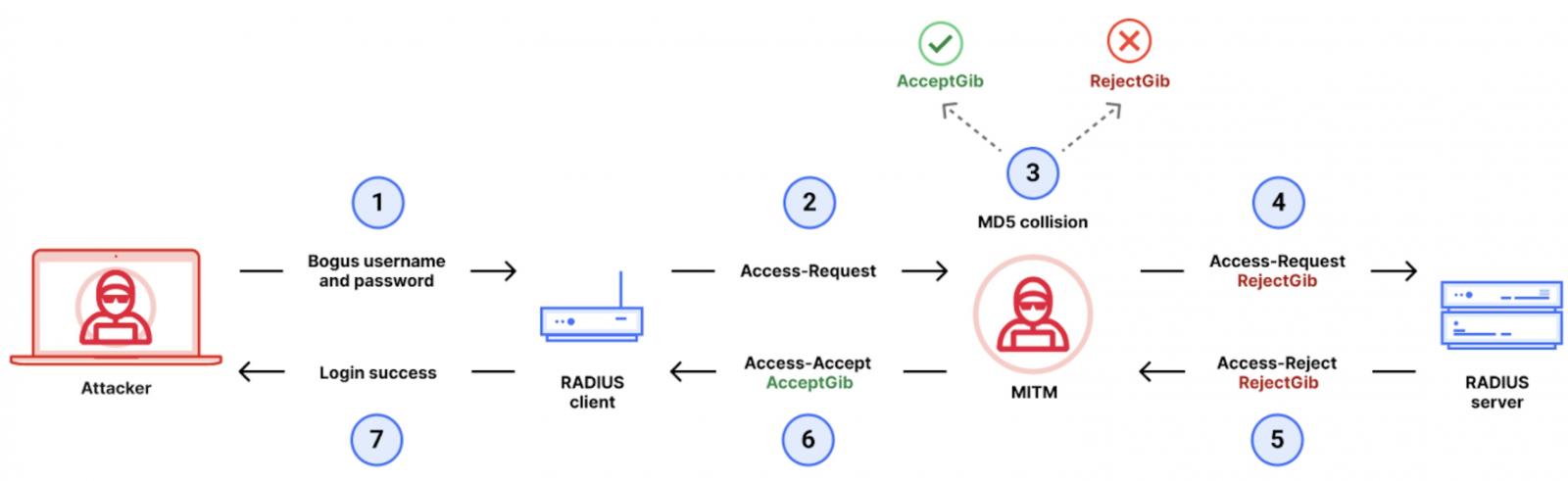
“The Blast-RADIUS attack allows a man-in-the-middle attacker between the RADIUS client and server to forge a valid protocol accept message in response to a failed authentication request,” the researchers behind it explained.
“This forgery could give the attacker access to network devices and services without the attacker guessing or brute forcing passwords or shared secrets. The attacker does not learn user credentials.
“An adversary exploiting our attack can escalate privileges from partial network access to being able to log into any device that uses RADIUS for authentication, or to assign itself arbitrary network privileges.”
The RADIUS protocol uses MD5 hashed requests and responses when performing authentication on a device. The researchers’ proof-of-concept exploit (which has yet to be shared) computes an MD5 chosen-prefix hash collision needed to forge a valid “Access-Accept” response to denote a successful authentication request. This forged MD5 hash is then injected into the network communication using the man-in-the-middle attack, allowing the attacker to log in.
The exploit takes 3 to 6 minutes to forge this MD5 hash, longer than the 30—to 60-second timeouts commonly used in practice for RADIUS.
However, each step of the collision algorithm used in the attack can be effectively parallelized and is suitable for hardware optimization, which would enable a well-resourced attacker to implement the attack using GPUs, FPGAs, or other more modern and faster hardware to achieve much quicker running times, possibly tens or hundreds of times faster.
”While an MD5 hash collision was first demonstrated in 2004, it was not thought to be possible to exploit this in the context of the RADIUS protocol,” the research team said.
“Our attack identifies a protocol vulnerability in the way RADIUS uses MD5 that allows the attacker to inject a malicious protocol attribute that produces a hash collision between the server-generated Response Authenticator and the attacker’s desired forged response packet.
“In addition, because our attack is online, the attacker needs to be able to compute a so-called chosen-prefix MD5 collision attack in minutes or seconds. The previous best reported chosen-prefix collision attack times took hours, and produced collisions that were not compatible with the RADIUS protocol.”
Since this attack does not compromise end-user credentials, there is nothing that end-users can do to protect against it. However, vendors and system admins who make and manage RADIUS devices are advised to follow these best practices and guidance.
To defend against this attack, network operators can upgrade to RADIUS over TLS (RADSEC), switch to “multihop” RADIUS deployments, and isolate RADIUS traffic from internet access using restricted-access management VLANs or TLS/ IPsec tunneling.